12 Best Kubernetes Security Tools You Need in 2026
One of the biggest challenges in cloud-native infrastructure is securing Kubernetes. Knowing which security tools to implement can be the difference between a hardened cluster and a vulnerable one.
In this article, we will explore the essential Kubernetes tools that you need to enforce security. With these tools, you’ll be able to build a defence in depth, and we will cover tools that help you shift-left, policy enforcement, runtime protection, and even compliance auditing.
TL;DR? Watch the video instead:
Shift-left Kubernetes Security tools
Shifting left means moving security earlier in the development lifecycle. Instead of discovering vulnerabilities and misconfigurations in production environments, you catch them during development or CI stages when they are cheaper and easier to fix.
1. KubeLinter
KubeLinter is your first line of defense, because it scans your Kubernetes manifests and Helm charts for misconfiguration before you actually deploy them. This tool excels at catching common issues, such as containers running as root, using the latest image tag, or missing resource requests and limits.
KubeLinter is now community-maintained, and its speed and simplicity make it perfect for CI/CD pipelines, where quick feedback is mandatory. A single kubelinter lint command can prevent security issues from ever reaching your cluster, making it a powerful component of any GitOps workflow.
2. Checkov
Checkov is a static analysis vulnerability and misconfiguration scanner that works with Terraform, CloudFormation, Kubernetes, and other infrastructure-as-code (IaC) frameworks.
It has over 1,000 built-in policies and identifies misconfigurations and compliance violations against standards like CIS, NIST, and others. It’s a powerful tool that should be leveraged in CI/CD pipelines where you need to enforce organizational standards before your infrastructure goes live.
3. Trivy
Trivy, from Aqua Security, detects vulnerabilities in container images, git repositories, IaC, and even Kubernetes clusters.
What sets Trivy apart is its versatility and speed. It scans for known vulnerabilities (CVEs), misconfigurations, exposed secrets, and even license issues. With recent updates, Trivy has enhanced its ability to scan running workloads, and its ability to generate Software Bills of Materials (SBOMs) addresses the demand for supply chain security transparency.
4. Kubescape
Kubescape, developed by ARMO, provides end-to-end security visibility from development to runtime. The platform scans both YAML manifests and live clusters, comparing them against frameworks such as NSA/CISA and MITRE ATT&CK.
Its standout feature is the risk-scoring system, combined with visual graphs, that help you quickly understand your security posture. While its runtime features are powerful, they often work best when combined with other specialized tools.
5. Cosign/Sigstore
Cosign, part of the Sigstore project, addresses supply chain security head-on. With Cosign, you can sign container images during your build process and verify the signatures before you deploy them.
This is important because it prevents tampered or unauthorized images from running in your clusters and allows you to easily confirm that your images are from trusted sources.
Policy Enforcement
After identifying issues through scanning, you need to enforce security policies that block these vulnerabilities or misconfigurations.
6. Kyverno
Kyverno is a CNCF incubating project, and its popularity has risen due to a simple reason–it lets you write your Kubernetes policies in YAML.

It can automatically validate, mutate, and generate resources. This makes it incredibly easy to enforce rules like "block all pods running as root" or "every new namespace needs a default network policy." Is it as flexible as its main competitor for super-complex logic? Some say no, but for most teams, its simplicity and Kubernetes-native feel make it the perfect choice.
7. OPA Gatekeeper
Open Policy Agent (OPA) with Gatekeeper represents the heavyweight option for policy enforcement in Kubernetes. OPA is a CNCF-graduated project and a general-purpose policy engine that works across your entire tech stack.
OPA uses Rego, a purpose-built declarative language for expressing its policies, which has a steeper learning curve than Kyverno’s YAML. If you need one policy language to standardize across multiple platforms and services, OPA is the industry standard.
Runtime Security and Networking
Even with perfect configuration scanning and policy enforcement, many threats can emerge after deployment. Runtime security tools provide continuous monitoring and protection for your workloads.
8. Falco
Falco is another graduated CNCF project, which is the gold standard for cloud-native threat detection.
Using eBPF, Falco hooks directly into the Linux kernel to observe system calls and container activity. Its rules are customizable and can detect anomalies such as unexpected shell access in containers or unauthorized file access. Falco needs some tuning to minimize false positives, but its deep visibility into runtime behavior is absolutely essential for your production workloads.
9. Cilium
Cilium has revolutionized K8s networking by leveraging eBPF to deliver high-performance networking and security at the kernel level, eliminating the overhead for traditional tools like iptables.
Cilium’s network policies operate on service identities and labels rather than IP addresses. It comes with Hubble, an observability tool that provides real-time visualization of service communication, making troubleshooting and security monitoring easier.
10. Calico
Calico is the battle-tested veteran of K8s networking, and its strength lies in its incredibly flexible, feature-rich network policy engine, which goes well beyond what standard Kubernetes policies can do.

While it may not have all the shiny performance perks of a pure eBPF solution like Cilium, its maturity and powerful policy features make it a trusted choice for locking down your cluster.
Auditing and compliance
Security isn’t just about prevention and detection. You should also demonstrate that your clusters meet security standards, which is done through auditing and compliance tools.
11. Kube-hunter
While Kube-hunter is no longer under active development and Aqua Security recommends Trivy instead, it is still worth mentioning for historical reasons.
Kube-hunter takes a different approach from other auditing tools, actively hunting for security weaknesses from an attacker’s perspective, attempting to exploit vulnerabilities rather than just detecting them.
12. Kube-bench
Kube-bench does one thing exceptionally well: it verifies that your K8s deployments actually follow the CIS Kubernetes Benchmark from the Center for Internet Security.
It runs as a simple job in your cluster and audits everything from control-plane components to worker-node configurations, providing clear results.
How Lens Kubernetes IDE can help with your Security Posture
Lens K8s IDE integrates smoothly with the security tools mentioned above, allowing users to view security scans, policy violations, and runtime alerts directly in the UI. With its AI assistant, Lens Prism, Lens K8s can help you troubleshoot security issues, providing fixes to your manifests, performing root cause analysis, and more.
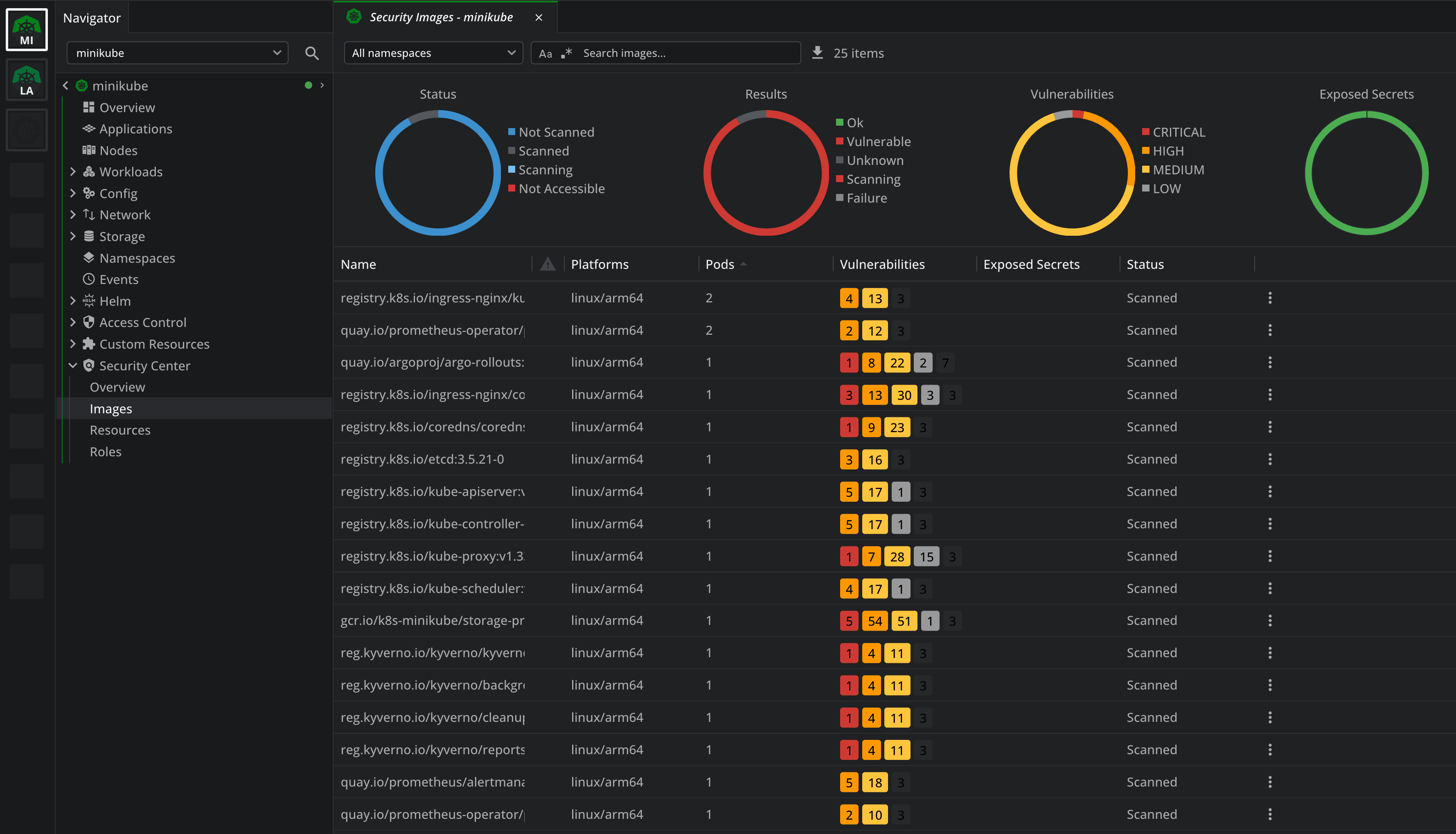
Lens K8s IDE also includes a built-in Security Center that uses the Trivy Operator, so you can see at a glance all issues across your images, roles, and resources.
Conclusion
Effective Kubernetes security requires implementing different tools in layers. You should start by shifting left, then ensure policy enforcement is enabled, add runtime protection, secure your networking, and maintain compliance.
There is no single tool that provides complete protection, but combining multiple tools creates the defence-in-depth approach that modern cloud-native security demands. Having Lens Kubernetes IDE in this equation helps you understand your security posture at a glance. If you want to see Lens K8s IDE in action, book a demo with one of our engineers.